The Importance of Testing Physical Security
In today’s world of sophisticated cyberattacks, organisations often focus heavily on digital defenses, implementing firewalls, antivirus solutions, and multi-factor authentication to safeguard their assets. However, one critical aspect of security often gets overlooked: physical security. An organisation’s physical security is the foundation of its overall protection strategy. If an attacker can physically access sensitive assets or systems, even the best cybersecurity measures can be rendered ineffective.
This is where physical security testing comes into play. By proactively assessing and addressing vulnerabilities in your physical defenses, you can identify gaps before malicious actors exploit them. Companies like Trinity offer specialised services to perform thorough and realistic physical security assessments using a variety of tactics, including reconnaissance, entry techniques, evasion strategies, social engineering, and device placement. Here’s why and how these elements matter.
Reconnaissance: Understanding the Environment
Before testing physical security, threat actors (ethical or otherwise) start with reconnaissance. This involves observing access points, staff routines, and the physical security controls in place.
A thorough understanding of employee behaviour, security patrol schedules, and building infrastructure is invaluable for planning an attack.
For example, an assessment team might:
- Review the landscape and footprint with online topograhical images.
- Observe staff members propping open doors during busy times.
- Review the methods of entry such as access control systems, RFID, PIN or key.
- Observe staff members using PIN code systems to capture the credentials.
- Identify unsecured delivery entrances or overlooked maintenance access points.
- Analyse how security cameras are positioned and where blind spots exist.
This step highlights how attackers can gather critical information without ever setting foot inside the premises.

Entry Tactics: Challenging The Defenses
Testing entry techniques is one of the most direct ways to assess physical security. Trinity’s methodology might include:
- Lock-picking or bypassing locks: Testing whether high-security locks can resist advanced techniques.
- Badge cloning: Exploiting weak RFID or NFC access card systems to duplicate credentials.
- Under-door tools: Exploiting gaps under doors to manipulate locks from the inside.
- Shimming: Using tools to bypass door latches or poorly installed hardware.
Such tests reveal whether physical barriers are truly secure or give a false sense of protection. If an attacker can breach these defenses, they gain access to sensitive areas like server rooms, document storage, or executive offices.

Evasion Tactics: Avoiding Detection
Once inside, the challenge shifts to remaining undetected. Evasion testing ensures that surveillance systems and staff vigilance are up to the task of identifying unauthorised individuals. Skilled testers evaluate:
- The effectiveness of security camera monitoring.
- Whether security staff notice unusual behaviors, like lingering in restricted areas.
- Response times when alarms or access control violations occur.
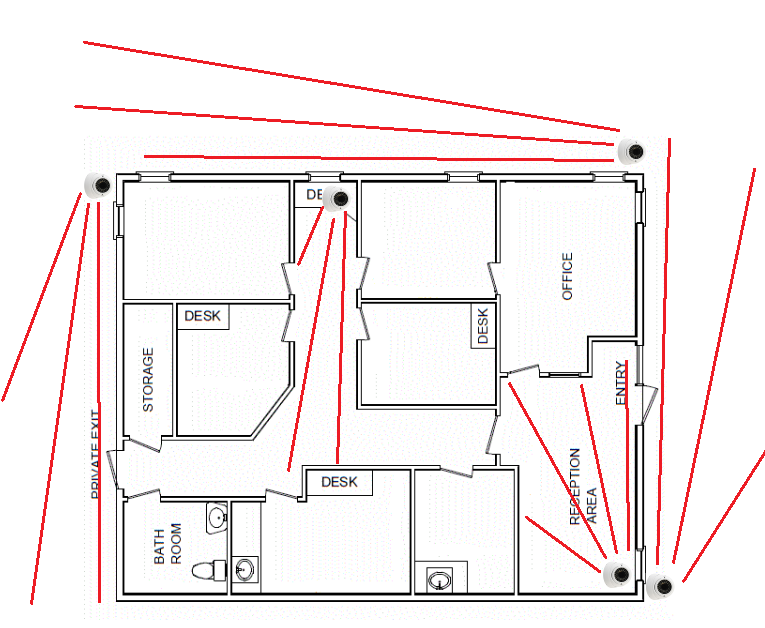
Weaknesses in these areas can allow intruders to stay on-site for extended periods, increasing the potential for theft or sabotage.
Social Engineering: The Human Element
One of the most critical aspects of physical security testing is assessing how employees respond to deception. Social engineering relies on exploiting trust and human error to gain unauthorised access. Methods might include:
- Impersonation: Posing as maintenance personnel, delivery drivers, or IT staff to bypass security checkpoints.
- Elicitation: Engaging in casual conversations to extract sensitive information, such as door codes or schedules.
Training employees to recognise and challenge suspicious behavior is essential, as even the best technology can be undermined by human vulnerabilities.
Device Placement: Simulating Advanced Threats
Lastly, testers may attempt to place rogue devices such as keyloggers, network taps, or hidden cameras, inside the organisation. These devices can compromise sensitive data or grant attackers ongoing access without the need for constant physical presence. Testing this aspect ensures that your physical security measures include regular inspections and swift detection of unauthorised devices.
The Value of Physical Security Testing
Investing in physical security testing is not just about identifying flaws; it’s about understanding how all components, technology, processes, and people work together to secure the organisation. A well-executed test:
- Uncovers vulnerabilities in access controls, surveillance, and staff protocols.
- Provides actionable recommendations to strengthen defenses.
- Prepares employees to recognise and respond to social engineering attacks.
- Improves overall security posture, reducing the risk of breaches.
By thinking like an attacker and testing the physical security comprehensively, organisations can stay one step ahead of potential threats. Physical security isn’t a secondary concern, it’s a critical part of modern risk management.
Please reach out to us on [email protected] or our contact page for more information.