A Technical Perspective on Cybersecurity Governance
In today’s digital landscape, cyber threats are an ever-present concern for organisations of all sizes. With the increasing sophistication of cybercriminals and the evolving nature of threats, it is critical for organisations to adopt proactive measures to safeguard their infrastructure. One such measure is what we at Trinity call a Business Breach Assessment (BBA), a comprehensive technical evaluation that parallels a Governance, Risk, and Compliance (GRC) gap assessment, but focuses specifically on identifying vulnerabilities, misconfigurations and architectural concerns within an organisation’s technical environment.
What is a Business Breach Assessment?
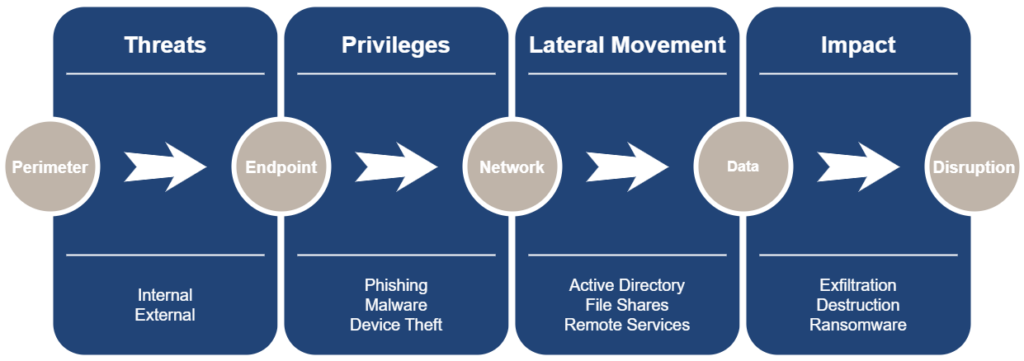
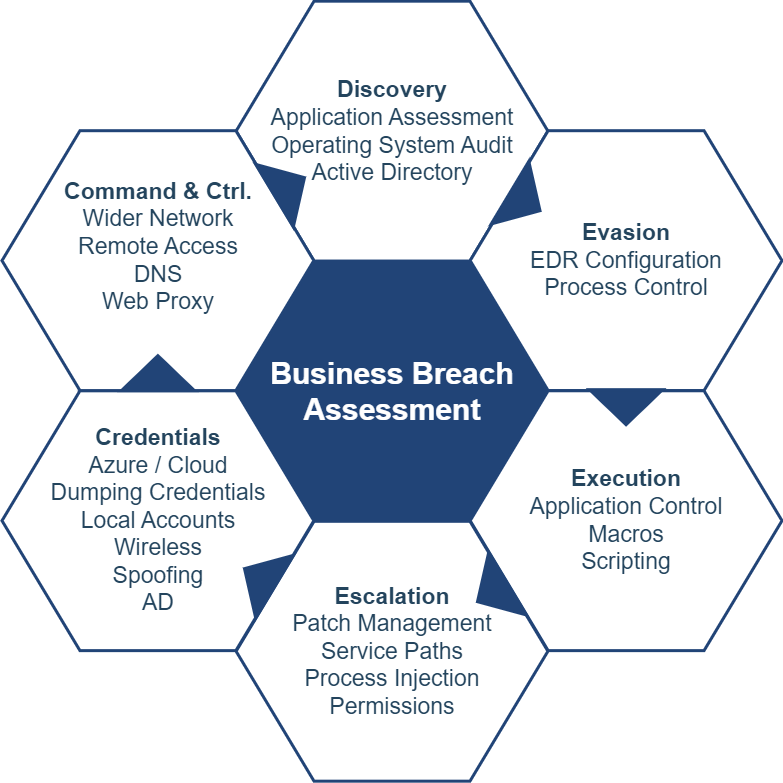
A Business Breach Assessment is a simulated cyber-attack designed to evaluate the security posture of an organisation’s IT infrastructure. Unlike traditional security assessments that focus solely on a subset of systems, internal or external network, compliance with industry standards or regulatory requirements, a BBA aims to identify real-world technical concerns that could be exploited by threat actors. This assessment encompasses a broad range of technical areas, including the perimeter, cloud services, Identity services, internal weaknesses, host hardening, endpoint protection and the wireless environment, providing a holistic view of an organisation’s cyber defence capabilities.
Why Organisations Should Consider a Business Breach Assessment
Comprehensive Weakness Identification: A BBA goes beyond the surface level to uncover hidden vulnerabilities that may not be apparent through standard penetration testing. By simulating various attack vectors, such as phishing, malware deployment, and lateral movement within the network, the assessment provides a detailed analysis of potential security threats. This comprehensive approach ensures that organisations are aware of their most critical vulnerabilities, enabling them to prioritise remediation efforts effectively, which we also provide guidance on in our reporting.
Proactive Risk Mitigation: In the rapidly changing cybersecurity landscape, waiting for an actual breach to occur before taking action can be devastating. A BBA allows organisations to take a proactive stance by identifying and addressing vulnerabilities before they can be exploited. This not only helps in preventing potential breaches but also minimises the impact of any incidents that do occur. By understanding their exposure to different types of cyber threats, organisations can implement targeted security measures to mitigate these risks.
Alignment with Industry Standards and Best Practices: A key component of a BBA is benchmarking an organisation’s security posture against industry standards and best practices, such as the ASD Essential 8. Additionally, adhering to these standards demonstrates a commitment to cybersecurity, which can strengthen an organisation’s reputation and trustworthiness among clients and partners.
Technical Insight for Informed Decision-Making: The detailed technical findings provided by a BBA offer invaluable insights into an organisation’s security environment. This includes assessments of cloud authentication and authorisation mechanisms, the configuration of wireless supplicants, and the deployment of Microsoft 365/Azure. These insights enable IT and security teams to make informed decisions about where to allocate resources and how to harden security measures. For example, identifying weak points in cloud services or the Azure Entra ID configuration allows for targeted improvements, such as enhancing multi-factor authentication (MFA), remote scripting capabilities or tightening access controls.
Tailored Recommendations and Remediation Strategies: One of the key deliverables of a BBA is a set of tailored recommendations for addressing identified vulnerabilities. This includes a root cause analysis of issues, along with prioritised remediation efforts. Organisations can use this information to develop a clear action plan, focusing on the most critical vulnerabilities first. This structured approach to remediation not only improves security posture but also optimises the use of resources, ensuring that efforts are focused on the areas that will have the greatest impact.
Conclusion
A Business Breach Assessment is an essential tool for organisations looking to bolster their cybersecurity defences. By providing a thorough technical evaluation of an organisation’s security posture, a BBA offers valuable insights into potential vulnerabilities and risks. This proactive approach not only helps in preventing breaches but also ensures alignment with industry standards and best practices. For organisations committed to maintaining a robust cybersecurity framework, investing in a Business Breach Assessment is a critical step toward achieving comprehensive protection and resilience against cyber threats, especially when a standard internal or external network penetration test result has been largely low risk in recent engagements.