Saving Money with Zero Trust
When considering Zero Trust, cost optimisation is not generally seen as one of its outcomes. Given the definition of Zero Trust as the assumption that all assets or users are untrusted, regardless of their location, or ownership, this implies the need to have controls that can evaluate endpoints, make suitable access decisions, and also enforce these. On the face of it, this seems complex and sounds like it might need a lot of controls. So how does Zero Trust deliver cost optimisation?
Let’s consider a simple network. Imagine we have completed the identification of actors and assets.
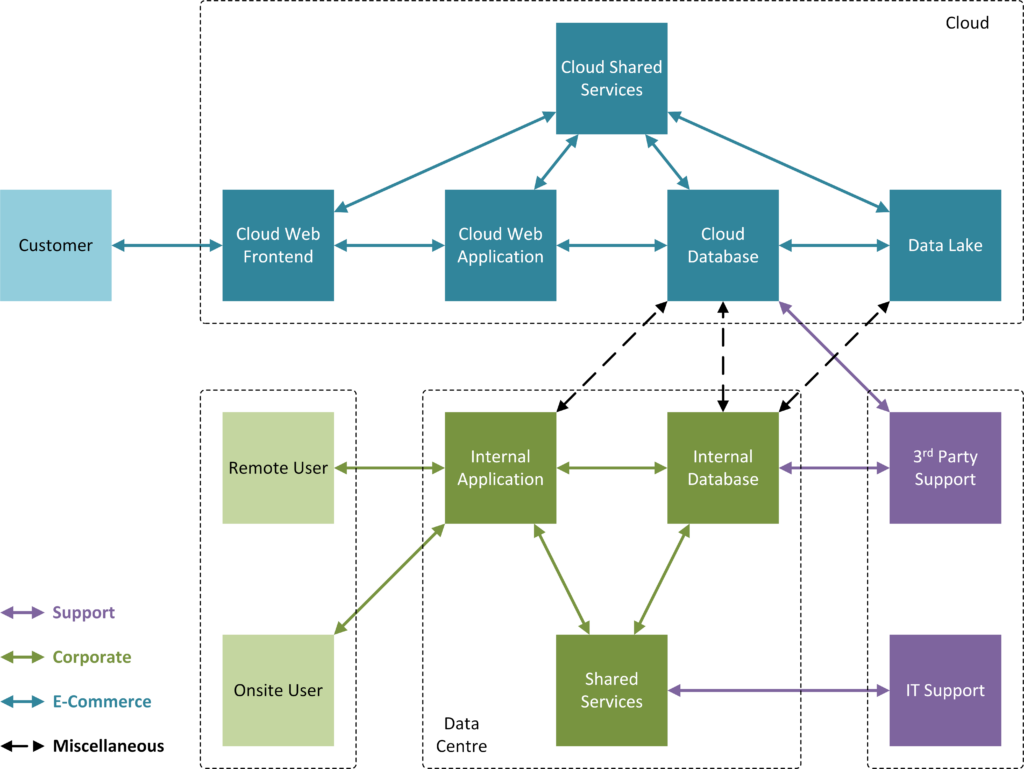
The diagram illustrates a relatively simple environment, which has the following:
- Customers, who want to use the business’ online platforms to purchase goods or services.
- Users, both on-premises, and remote, who access internal business applications (either through a VPN, or an on-premises network)
- A data centre, which contains application components like an on-prem database and some internal applications for corporate users.
- A cloud instance that contains a web app front-end, middleware, database, and data lake.
- 3rd party and remote IT support for internal systems.
For the sake of argument, let’s consider some basic communication between actors and assets. The colour coded arrows indicate communications happening as part of business processes. In this case:
- Let’s lump all the customer related processes into a bucket. Let’s call this ‘E-commerce’, in blue.
- All the internal corporate processes (finance, procurement, development, logistics, etc.) related to supporting the business. Let’s call this ‘Corporate’, in green.
- Internal and external support for systems. Let’s label this ‘Support’, in purple.
- There are some dashed lines, these are common to both E-commerce and Corporate processes.
A simplistic interpretation of Zero Trust implies all communications between assets and actors involved in each of these processes (i.e., on ALL lines between assets/actors on the diagram). Policy will have to be added somehow. Let’s add some technical controls to achieve this. We’re not going to be completely naive about this, so let’s add some reasonably common controls to achieve our needs, and we’ll try not to use a control for each communication.
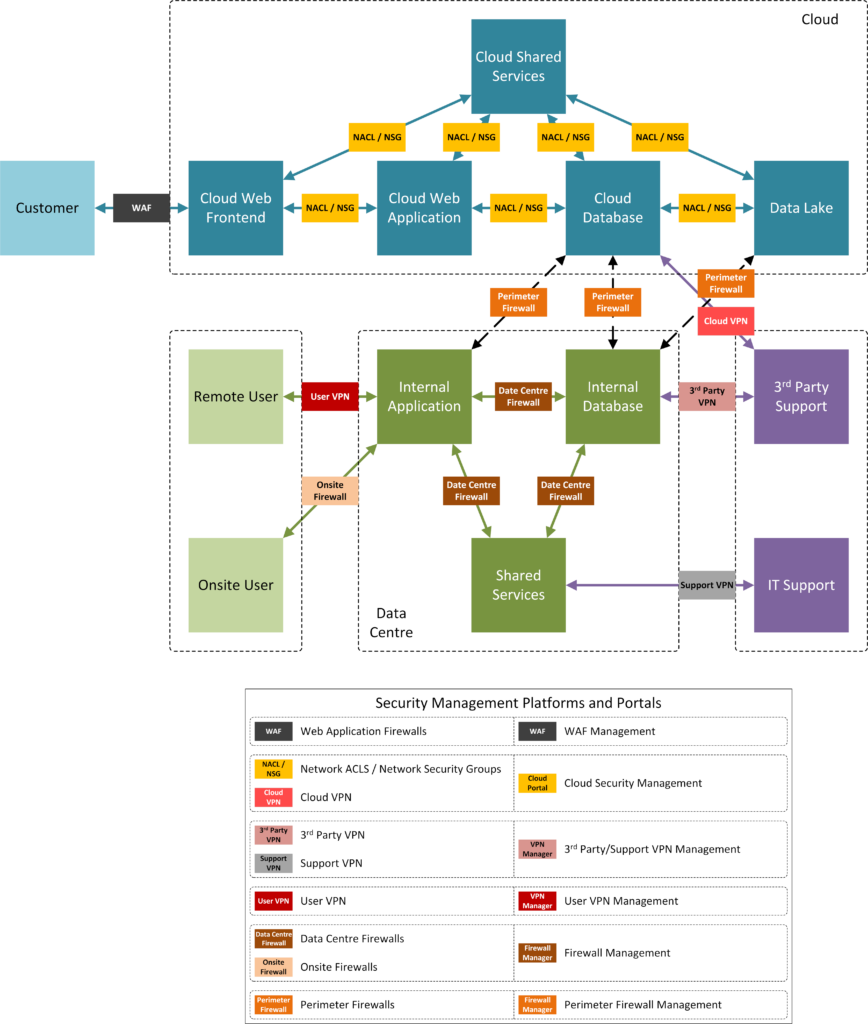
Now we have a whole lot of technical controls regulating how entities in the network communicate. Lots of disparate controls bring with them a number of problems. Chief among these being the difficulty in maintaining a consistent policy across the organisation (for example, policy consistency across onsite and remote users) and the cost and operational complexity.
It’s probably apparent at this point that some of these controls are good candidates for collapsing into a single solution. SASE is a terrific way to achieve a huge amount of consolidation. In our example, SASE can subsume the following:
- All the various VPNs (Cloud, 3rd Party, Support, User) through Zero Trust Network Access (ZTNA) functionality.
- The on-premises firewalls through Firewall-as-a-Service (FWaaS) functionality. In effect, all on-premises users would be considered exactly the same as remote users. The site would simply require Internet access.
- The perimeter firewalls through FWaaS as well.
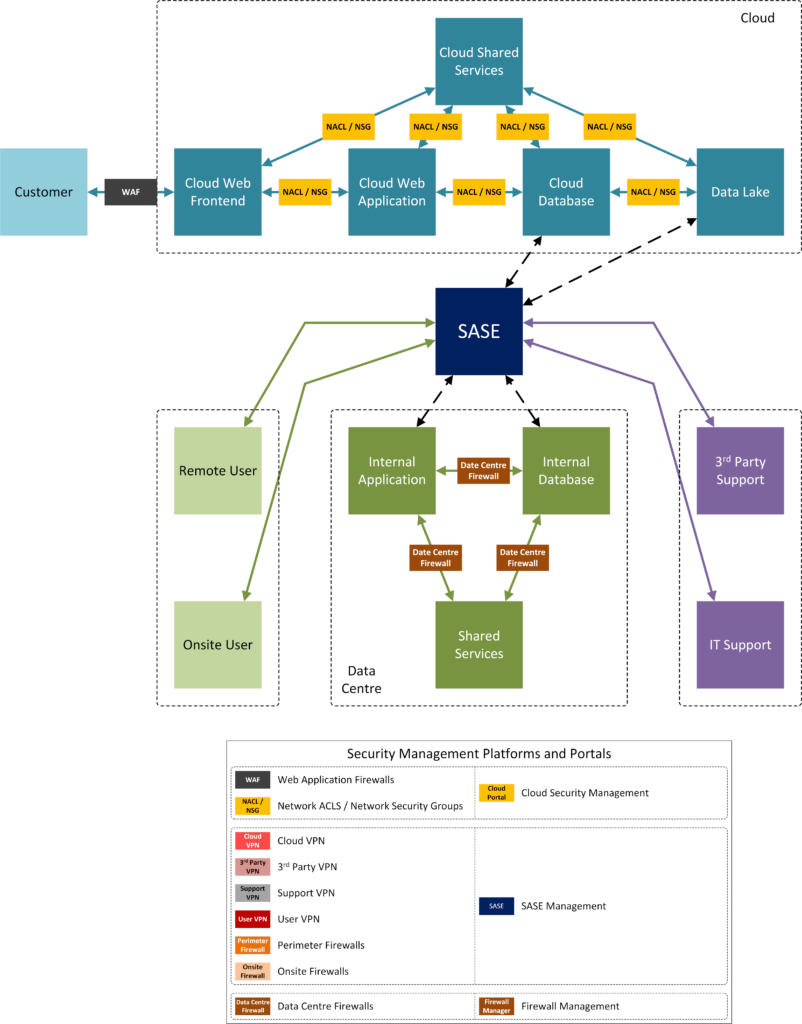
That’s a lot fewer separate controls to have to worry about. Obviously TCOs would have to be compared to determine if the consolidated control is in fact going to be cheaper than multiple controls, but at least you now have a good idea of what can be consolidated, and this process can help as a foundation for a good business case.
How do you actually go about achieving Zero Trust in your environment?
Let’s examine a process for implementing Zero Trust. Note, this is simply ‘a’ process, not ‘the’ process. There is presently no industry accepted process for achieving Zero Trust. The process we have chosen is described in NIST SP 800-207. Section 7.3 is the most relevant, as it describes a process for introducing Zero Trust architecture into an organisation, which is going to be the starting point for most people.
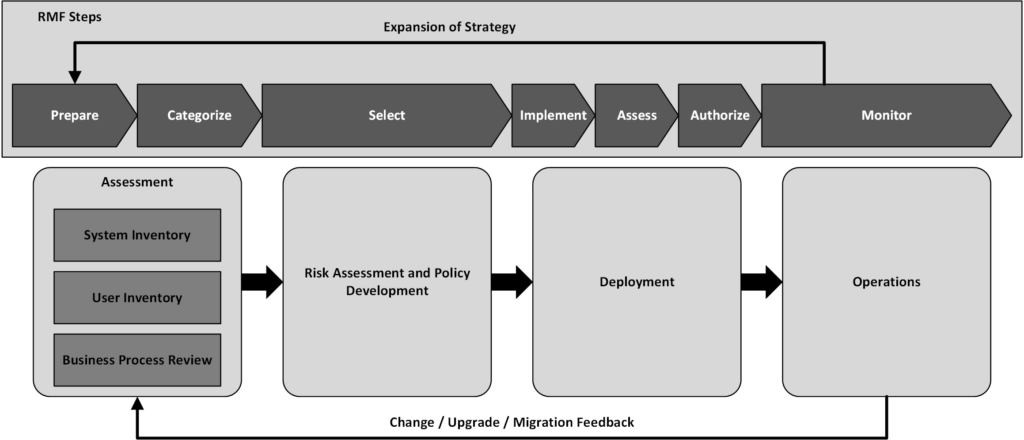
The process can be summarised below:
1. Identify Actors on the Enterprise
2. Identify Assets Owned by the Enterprise
3. Identify Key Processes and Evaluate Risks Associated with Executing Process
4. Formulating Policies for the ZTA (Zero Trust Architecture) Candidate
5. Identifying Candidate Solutions
6. Initial Deployment and Monitoring
7. Expanding the ZTA
This is an excellent overall process. The only modifications we would make would be the introduce a step 2.5 where we identify existing controls (remember, we’re only introducing Zero Trust in an existing network with existing controls, not starting from scratch), and make sure to include these controls in step 5 when evaluation candidate solutions.
The first three steps rely on a significant amount of information early on to guide decision making. Our experience has shown that these are the foundation for the success of this endeavour. Organisations sometimes struggle at this foundational level. We have developed a service to help organisations understand their technology estates and produce an accurate picture of actors, assets and existing controls. If you’d like to know more about this, then please reach out.
Wherever you are on your Zero Trust journey, Trinity Cyber Security can help you along the way. From identification of assets and controls all the way to Zero Trust product selection and implementation (including the potential consolidation benefits along the way).
Please reach out to us on [email protected] or our contact page for more information.